In the world of cybersecurity, there’s always a new threat on the horizon. The latest trick used by threat actors to dupe unsuspecting victims is to highjack the communications of the very institutions meant to keep us safe.
Email Server Hacked
Recently, the FBI (Federal Bureau of Investigation)‘s own email server was successfully hacked, sending out fake cybersecurity alerts to thousands. The incident was publicly disclosed by International Threat Intelligence Organization, Spamhaus, on the 13th of November.
The FBI later confirmed the incident in a statement you can find here.
Specifically, the hackers compromised and sent spam emails from the FBI Criminal Justice Information Services (CJIS) ‘s Law Enforcement Enterprise Portal (LEEP). LEEP is meant to be a secure platform for law enforcement agencies, intelligence groups, and criminal justice entities. It offers web-based investigative tools, analytical resources, and networking opportunities for state and local law enforcement.
Instead of simply spoofing the FBI’s email address, the hackers could therefore use a legitimate email address to send the false alerts, namely “[email protected][.]gov.” The email contained the subject line: “Urgent: Threat actor in systems.”
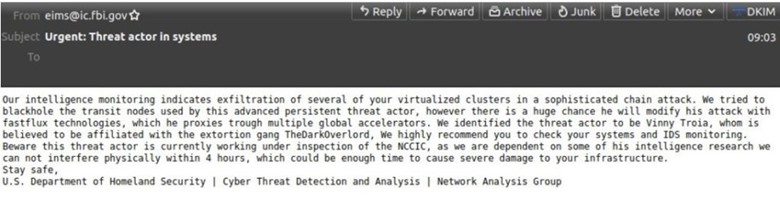
Screen capture received by Brian Krebs of Krebs on Security
A screengrab of the false alert received by Brian Krebs of Krebs on Security:
So far, it seems as if the primary objective of the hack was to frame Vinny Troia, a security researcher and founder of dark web intelligence firms Night Lion Security and Shadowbyte. The emails also claimed that Troia is actively affiliated with the hacking gang TheDarkOverlord.
However, in the days following the attack, the notorious hacker pompompurin claimed responsibility for the hack. In an exclusive interview with Brian Krebs, he claimed to have perpetrated the attack as an attempt to expose the glaring shortcomings in the FBI’s cybersecurity systems.
Apparently, it was a simple software misconfiguration that opened the doors for pompompurin. He then abused the multi-factor authentication system to leak the one-time password needed to register an account right from the HTML of the web page.
At first, the hack seemed to be just the latest in a long line of smear campaigns launched against Troia in retaliation for disclosing information on TheDarkOverlord. According to Marcus Hutchins, a researcher from Kryptos Logic, the actor had previously attempted to implicate Troia in an attack on ElasticSearch and hacked various accounts of his.
For whatever reason, pompompurin has also made a habit of targeting Troia in showcasing his hacking skills.
A Dangerous Precedent Set
For now, it seems as if the FBI has dodged a bullet as this vulnerability was not exploited by a more sinister threat actor. However, it showed that no one, not even the FBI, can afford to become complacent regarding cybersecurity. Be it in the United States, Toronto Canada or anywhere else in the world, all organizations must perform penetration tests (pentesting) and vulnerability assessments on their internal and external infrastructures on a regular basis.
Regardless, this incident sets a dangerous precedent. If hackers can use legitimate emails in attempts to phish, infect, or otherwise scam victims, their likelihood of success is much higher. A highly trusted source, such as the FBI’s email servers, is the last place the public would expect such attempts to come from. Therefore, it is important to provide employees with cybersecurity awareness training to help organizations detect and parry phishing and social engineering attacks. It’s important to stay vigilant and anticipate our adversaries. Keep your eyes peeled!


