Target Identified: Attack Initiated
By Keith Kaniut
On May 11, 2022 The Record media site reported that a Canadian company that provided Adversary Training for military fighter pilots using an eclectic collection of US and European military jets, had been attacked by ransomware using the typical tactics used in most ransomware attacks. Below is a fictional narrative that speculates how this company’s network might have been compromised. In a brief statement the company confirmed the event and its investigation of the incident. The type of company targeted makes this story unusual.

Condensation forming on the wings of an F-16 during flight.
“Rocker” Rokowski had been targeted before. In fact, that was his job. After a military career flying fighter jets he’d found the perfect civilian job for his skills – a Montreal Canada-based company called Top Aces that provided adversary fighter jet training as a defense contractor to the U.S., Germany, Israel and other countries in need of this specialized training. His job was to be the Bad Guy; to conduct simulated fighter jet attacks against the customers’ pilots and teach them how to both counter those attacks and to get the upper hand. If everyone was teaching and learning properly, he would be targeted and “shot down” (simulated) before he could do the same to the customer.
But this attack was different. He wasn’t airborne; he was sitting at his desk answering email. The email said it was from his boss and required immediate attention. There was a customer audit or something and he just needed to click the link to complete a survey. He thought he had enough time before his next flight and clicked the link. Then this message appeared on his monitor:
Warning!!
Antivirus has detected an intruder on this computer. Your PC has been infected by a dangerous virus and all your data is being encrypted. Click the link below to advise the IT department to avoid further damage. Do not delay! Failure to comply will result in immediate termination of your services.
A colorful expletive crossed his mind. This wasn’t good. He didn’t have time for this and knew he was way outside his area of expertise. He clicked the provided link and headed for the briefing room for the next flight. He’d tell the IT guys about it when he returned.
As he left the room, somewhere in the cloud a bot operator associated with the LockBit ransomware group began encrypting and stealing the company data. Shortly thereafter the Top Aces cybersecurity team discovered their company’s name on a leak site associated with the LockBit group along with a threat to release 44GB of stolen data if they didn’t pay.
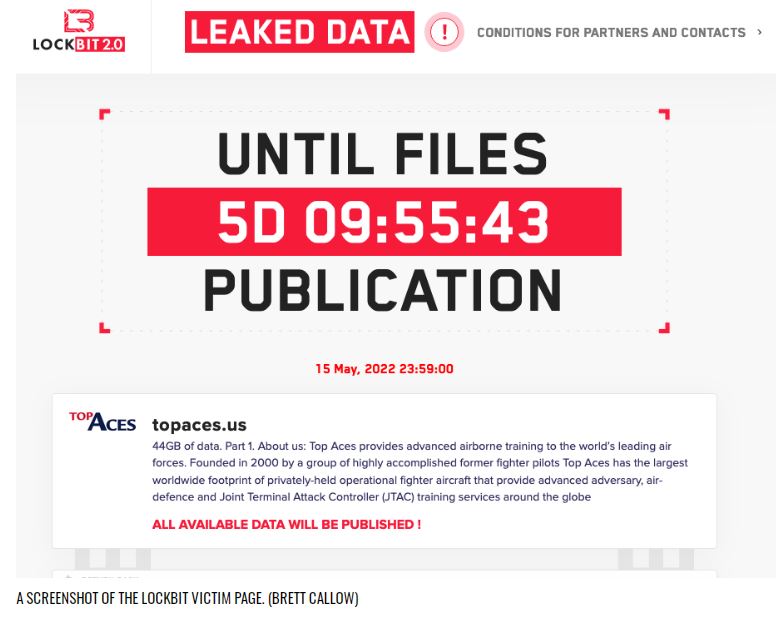
The company Top Aces was founded in 2000 by former fighter pilots and is the sole private provider of adversary air training to the Canadian and German armed forces. The company is the only company flying privately-owned F-16 Falcon jets as adversary aircraft in addition to modernized Dornier Alpha Jets, the Douglass A-4N Skyhawk and the Bombardier Learjet. In October 18, 2019 it won a USD $6.4M contract to provide the U.S. Air Force with adversary air training.
The Record article included quotes from Emissoft threat analyst Brett Callow noting that attacks on defense sector companies should concern everyone because “there’s no way of knowing where the stolen data may end up.” Even if the ransom is paid.
It should be obvious that threat actors who steal or encrypt data are motivated by the profit and would love to sell valuable data to hostile governments or terrorists. Brett Callow specifically mentioned two previous defense supply chain attacks – Visser Precision a Lockheed-Martin parts supplier, and Westech International, a military contractor supporting the Minuteman III nuclear missile deterrent system.
According to the BlackFog site report for 2022, the Conti and Lapsus$ ransomware groups are the two most active groups so far in 2022, accounting for 27.3% and 13.6% of the attacks respectively. The BlackCat and LockBit groups were in 3rd and 4th place, accounting for another 9.1% and 7.6%. The targets were in nearly every industry as well as local and state governments. Cyber insurers have been forced to raise their rates because of the significant increase in attacks.
Bottom line: No company or organization is immune from these attacks. Your best defense is one that ensures your employees are fully trained to “Never Trust and Always Verify” all emails and calls. If you can stop your people from reflexively clicking the links or opening infected documents, your company becomes a more hardened target. But remember, it only takes one less vigilant, or disgruntled employee to open the back door for bad actors. Moreover, your organization’s network should enforce a Zero Trust policy and adhere to the Principle-of-Least-Privilege (PoLP). In other words, this means your cybersecurity infrastructure needs to be intelligently designed to limit internal access to just what is necessary for people to maintain business operations.
That means ensuring that even if one of your computers is compromised, it won’t open your entire network to an intruder, allowing them access to your company’s intellectual property, PII, source code and financial information – also known as: “your Crown Jewels”. What is the solution to this problem? A comprehensive penetration test and regular vulnerability assessments by a certified cybersecurity expert can check your defenses in this area and identify any vulnerabilities in your cybersecurity wall.
And that’s where Ardent Security comes in. This is the home adversary environment we fly in!
Sure, it’s not as glamorous as being a fighter pilot, but let’s be frank; a fighter pilot wouldn’t be much help with this problem unless you know the location of the ransomware servers and intend to conduct an aerial strike on them. (For legal purposes, our lawyers have advised us not to recommend that anyway…)
Call Ardent Security today.
647-478-2600
We can help.


